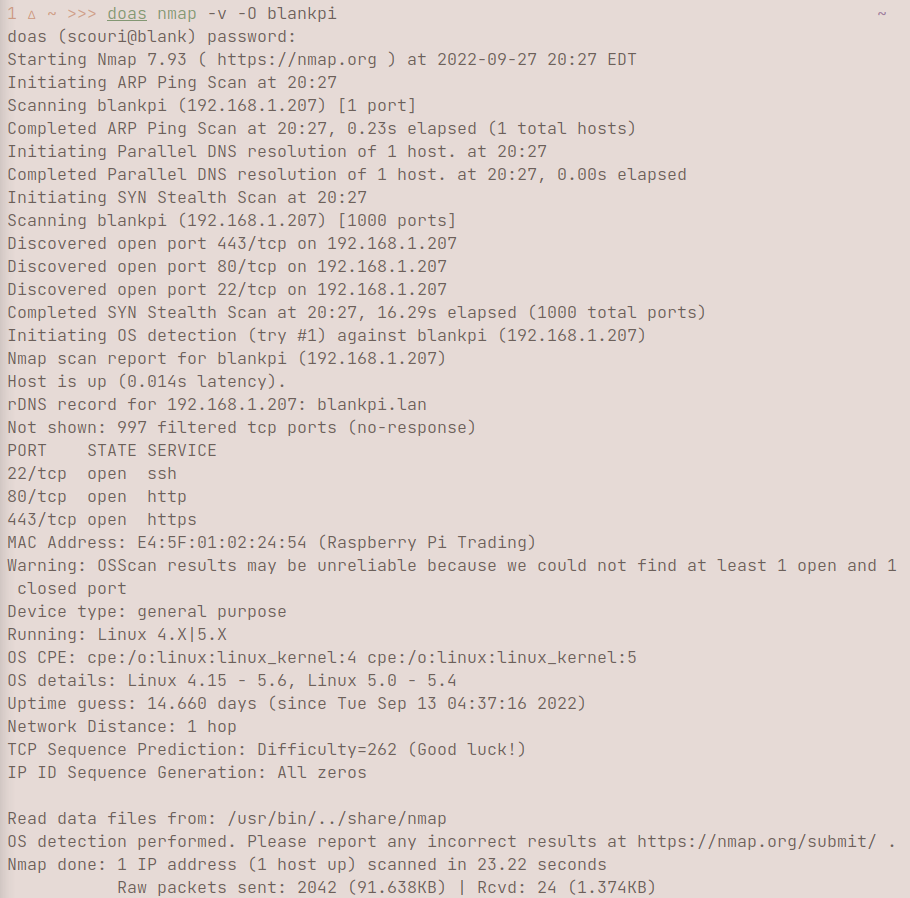
{:title "Nmap usage" :layout :post :tags "Networking" }
nmap hostname does a basic TCP SYN scan for the first 1000 ports open on the host, which doesn't show much besides the ports. 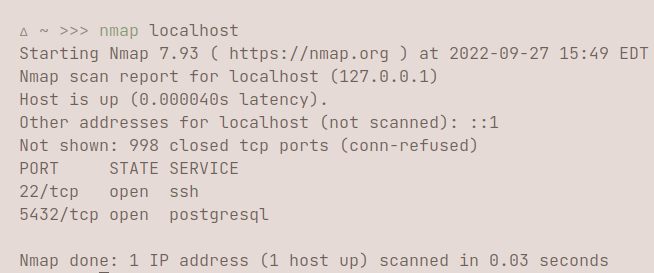 I personally prefer getting more verbosity by simply adding -v or -vv to the parameters. Simply by adding v, you can get more indepth information about the host.
I personally prefer getting more verbosity by simply adding -v or -vv to the parameters. Simply by adding v, you can get more indepth information about the host. 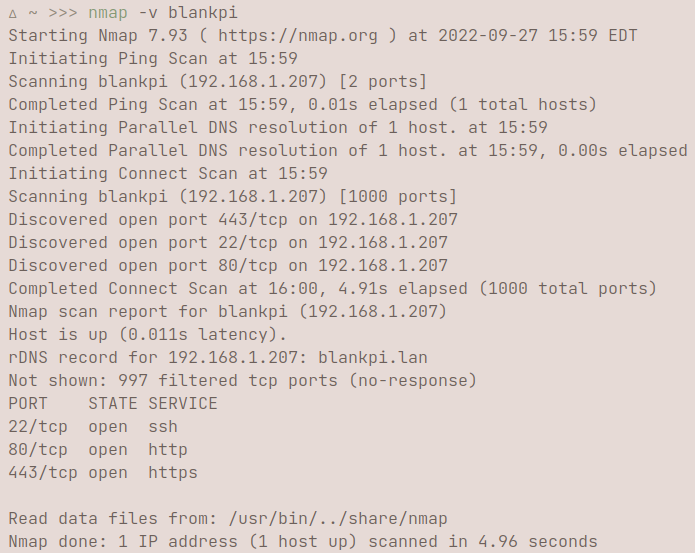 If you're interested in doing a ping scan, you can use -sn. A ping scan identifies all of the IP addresses that are online and on the network of the provided host. For example, when I use my RaspberryPi's hostname, I can see all the device hostnames/IP addresses that are connected to the internet, ranging from phones, computers, TVs, etc. You would do this by using
If you're interested in doing a ping scan, you can use -sn. A ping scan identifies all of the IP addresses that are online and on the network of the provided host. For example, when I use my RaspberryPi's hostname, I can see all the device hostnames/IP addresses that are connected to the internet, ranging from phones, computers, TVs, etc. You would do this by using nmap -sn hostname/24. /24 tells nmap to scan all the addresses from 192.168.100.0 to 192.168.100.255, or rather 256 hosts on the network. IPv4 addresses are 32 bits, every period signifies a section of an IP address, so the /24 tells nmap to only vary the last 8 bits of an address when scanning.nmap -p 1-65535 localhost scans every port. You can also write this as nmap -p- localhost, which produces the same output. You can specify ports using ranges, or with single ports, as shown here: 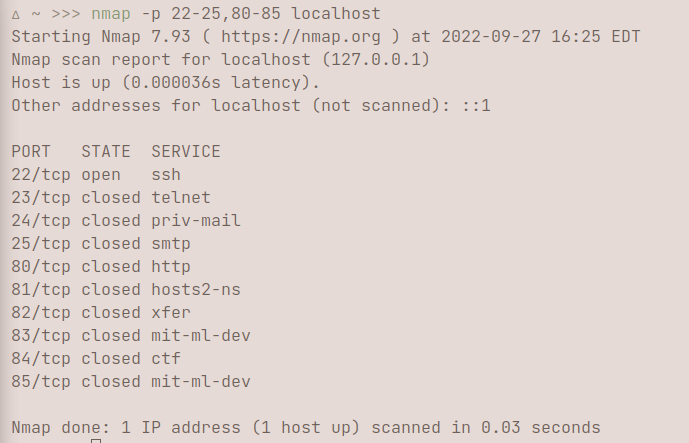 This shows the status of every port, ranging from port 22-25, to port 80-85.
This shows the status of every port, ranging from port 22-25, to port 80-85. 